- Skimming and card cloning aren’t the same. First is the method used to steal card data, while cloning is creating duplicate cards with that stolen information. Skimming is the first step in the cloning process.
- Cardholders can dispute fraudulent charges as soon as they notice them. Card issuers typically provide provisional credit within 24-48 hours while investigating the claim.
- You won’t face criminal charges for unknowingly accepting cloned cards. However, you may lose money through chargebacks and could face compliance issues if you’re not following security standards.
You’ve probably heard about card cloning in the news, but what does it actually mean for your business? Essentially, it is when some guy with too much time on his hands figures out how to copy the data from your customer’s card and make a new one.
Once they have the data, they put it on a blank card and use it just like the real thing. Your customers don’t even know it happened until they see charges they didn’t make.
But how exactly do they pull this off? And what can you actually do about it? Let’s break down all the essentials you need to know.
How Card Cloning Works?
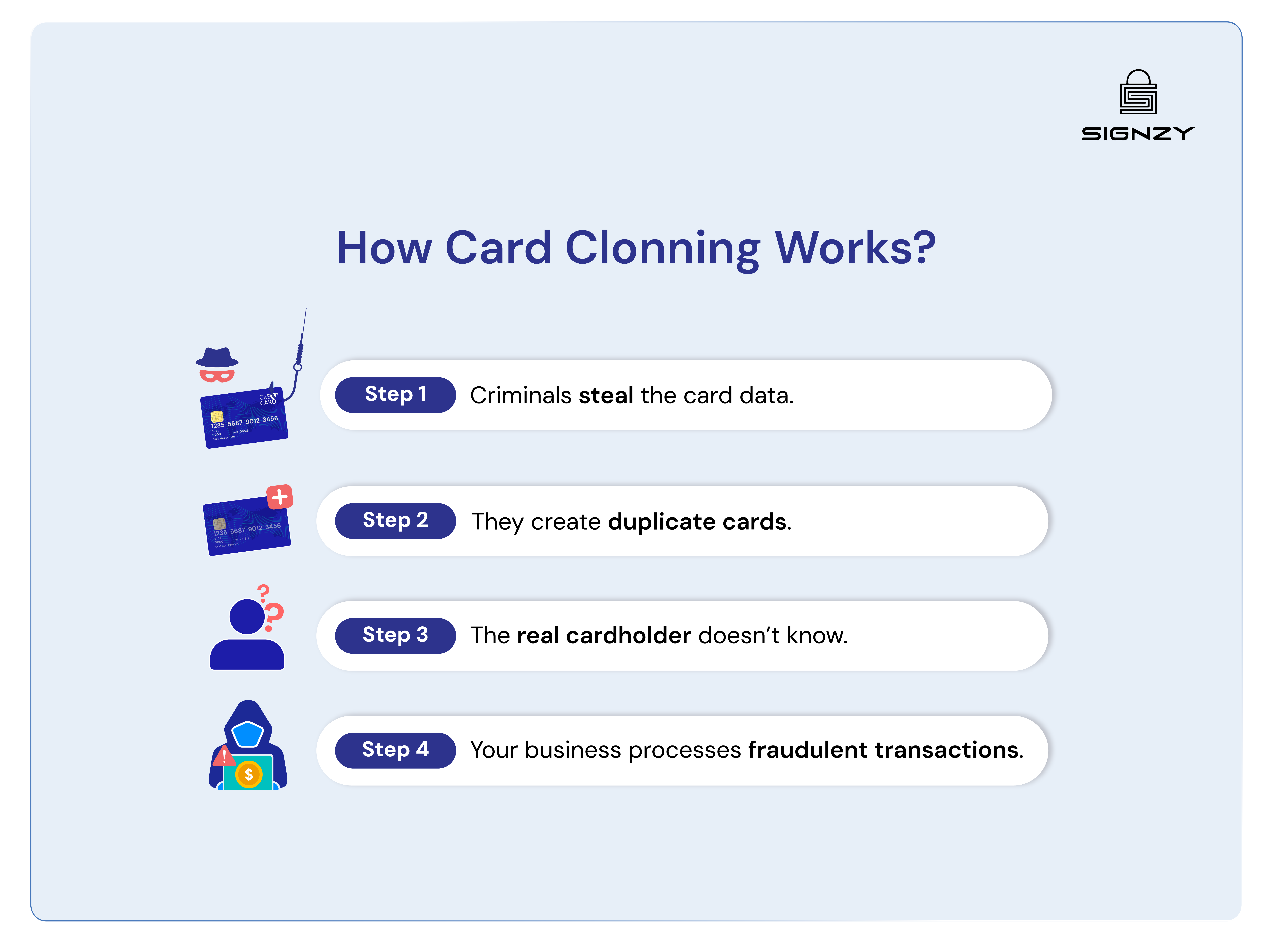
I already gave a gist of what card cloning is and how it works above itself. Here, I am going to expand a bit more on it to help you understand the problem better so you can tackle it well.
Stage 1: Criminals steal the card data
They attach these little skimming devices to ATMs, gas station pumps, or restaurant card readers. When your customers swipe their cards, the skimmer captures all their card details – the numbers, expiration date, everything.
They can also steal info from contactless card transactions using a technique called “NFC sniffing”. Some skimmers are so well-made they look exactly like part of the original machine.
Stage 2: They create duplicate cards
Back at their setup, they take all that stolen information and burn it onto blank cards. These aren’t just random fake cards – they have your customer’s actual card data on them. When someone uses one of these cloned cards, it processes exactly like the real card would.
Stage 3: The real cardholder doesn’t know
Your customer keeps using their original card normally. Since the card wasn’t physically stolen, everything works fine on their end. They might not notice unauthorized charges for weeks or even months, especially if the fraudster makes small purchases to avoid detection. Many criminals will test cards with small purchases first before making larger ones.
Stage 4: Your business processes fraudulent transactions
When someone uses a cloned card at your location, you have no way to tell it’s fake. The transaction goes through normally because it’s using real card data from a legitimate account.
By the time the legitimate cardholder disputes the charge, you’re facing a chargeback and loss of both merchandise and payment.
How to Detect Cloned Cards During Transactions
Spotting cloned cards before you complete the transaction can save your business from chargebacks and losses.
| Warning Sign | What to Look For | Why It Matters |
| Physical Card Issues | Magnetic stripe looks newer/shinier than the rest of the card, numbers don’t line up properly, or the card feels cheap or has the wrong thickness. | Cloned cards often use lower-quality materials or have reprinted elements |
| Signature Strip Problems. | The strip looks peeled off and reapplied, doesn’t match card age, and there is obvious tampering. | Criminals replace original strips to add fake signatures. |
| Customer Behavior | Nervous/hurried, doesn’t know if the card is debit/credit, avoids showing ID, buying high-value, easily resold items. | Fraudsters want to complete transactions quickly before detection |
| Data Mismatches. | The cardholder name on-screen differs from the card, the billing address doesn’t match, and multiple verification failures. | Magnetic stripe data doesn’t match what’s printed on the card surface. |
Most payment processors offer real-time verification tools like address verification and CVV checking that reference official card network databases.
According to Visa’s merchant guidelines, transactions failing multiple verification checks have significantly higher fraud risk. Enable these tools in your payment system – they’re your first line of defense against accepting cloned cards.
What to Do When You Accept a Cloned Card
Finding out you’ve accepted a cloned card usually happens when you get a chargeback notification, but quick action can help protect your business and assist law enforcement.
Before I go into where to do what, document everything as soon as possible.
Keep copies of the original transaction receipt, any ID the customer showed, and security camera footage from the time of purchase. Then, you can follow this five-step process.
- Report to your payment processor first. Contact your merchant services provider as soon as you discover the fraudulent transaction. They can flag the card number in their system and guide you through their specific fraud reporting process. Most processors have dedicated fraud hotlines available 24/7.
- File a police report. Even if the dollar amount seems small, report the incident to local law enforcement. They track fraud patterns, and your report might connect to a larger investigation. Get a copy of the police report number for your records.
- Notify the card brands. Help them track cloned cards. Your processor can usually handle this reporting for you but confirm they’re doing it.
- Prepare for the chargeback dispute. Gather all your documentation and submit it through your processor’s chargeback system if anything arises. Include the police report, any video evidence, and proof that you followed proper card acceptance procedures. The card networks have specific timeframes for disputes, so act quickly.
- Review your security procedures. Use this incident to evaluate your current fraud prevention measures. Consider upgrading your payment terminals, adding more verification steps like face match APIs, or providing additional staff training.
Taking these steps won’t guarantee you’ll win a chargeback dispute, but proper documentation and reporting significantly improve your chances and help prevent future fraud at your business.
Tips to Prevent Card Cloning
Preventing card cloning at your business requires a mix of technology, procedures, and staff awareness.
-
Use EMV chip card readers
Get chip card readers if you don’t have them already. Chip cards create a unique code for each transaction that can’t be copied like the old magnetic stripe data. When customers try to swipe instead of inserting their chip card, make them use the chip reader. It takes a few extra seconds but cuts fraud way down.
-
Turn on the address and CVV verification
Most payment systems have these verification tools built in, but you need to actually turn them on. Address verification checks if the billing address matches what the customer gives you. CVV checking confirms that the three-digit code is on the back of the card. When these checks fail, that’s a big red flag.
-
Train your staff to spot problems
Your employees need to know what to watch for. Customers who seem nervous or don’t know if their card is debit or credit. Cards that look tampered with or feel different. People are buying expensive stuff with beat-up old cards. Run through these scenarios with your team so they know what to do.
-
Check your card readers every day
Look at your payment terminals each morning. Criminals attach skimming devices to steal card data, and these devices often look like they belong there. If something feels loose or looks different from yesterday, don’t use it. Call the cops first, then your payment processor.
-
Add identity verification for big purchases
For large transactions or when something feels off, consider using identity verification services. These API-driven tools can instantly check if the person using the card is actually the cardholder by cross-referencing official databases. Especially helpful if you sell high-value items or deal with a lot of fraud in your industry.
These prevention methods work better when you use several together. No single approach stops everything, but criminals look for easy targets. Make your business harder to hit, and they’ll go somewhere else.
FAQs
Can chip cards be cloned?
Chip cards are much harder to clone than magnetic stripe cards because they generate unique codes for each transaction. However, criminals can still steal chip card data if the magnetic stripe is also used.
How long does it take to detect card cloning?
Most cardholders don’t notice cloned card usage for 2-4 weeks until they review their statements. Businesses typically find out when they receive chargeback notifications from the card issuer.
Do I need special equipment to detect cloned cards?
Basic EMV chip readers and verification tools built into most payment systems can help detect many cloned cards. Additional fraud detection services are available for higher-risk businesses.
Are online transactions safer from card cloning?
Yes, online transactions are much safer than cloned cards. Most online systems now require OTPs, 3D Secure authentication, or other verification methods that cloned cards can’t provide.