Complete Guide to Biometric Verification Systems for Businesses [2025]
September 8, 2025
7 minutes read
- Biometric verification systems are replacing traditional passwords by using unique physical and behavioral traits, offering superior security while improving user experience across industries worldwide.
- From smartphone unlocking to airport security, biometric systems are deployed across financial services, healthcare, transportation, retail, and education sectors for enhanced security and convenience.
- Systems convert biological traits into encrypted mathematical templates rather than storing actual images, making them virtually impossible to reverse-engineer while maintaining fast processing speeds.
Alright, real talk – I just watched a 67-year-old neighbour unlock his banking app with his face in about two seconds, while I’m still over here typing passwords like it’s 1995.
That’s basically where we are with customer verification right now. Your customers are living in the future on their personal devices, but then they hit your onboarding flow and suddenly they’re back to “What was your first pet’s name?”
The thing is, your customers already trust their face or fingerprint to unlock phones worth $1000+. They’re not scared of technology. They’re just waiting for you to catch up.
So if you’re thinking about upgrading your customer onboarding, let’s dig into what biometric verification actually looks like in practice.
What is a Biometric Identity Verification System?
A biometric identity verification system is automated software that recognizes people by their unique physical or behavioral traits – like fingerprints, faces, or voices – instead of relying on passwords or ID cards.
The technology isn’t new. We’ve used thumbprints since ancient times – but AI-powered automation is recent. These systems work because biological traits are statistically unique and relatively permanent. Instead of storing actual fingerprints or photos, they create encrypted mathematical templates from unique features, making them secure and fast to process.
The appeal is simple: your customers already trust biometrics to unlock phones, but traditional passwords can be forgotten, stolen, or hacked. Biometrics use the person themselves as the key, solving authentication headaches while improving security.
How Do Biometric Identity Verification Systems Work?
Every biometric scan operates through the same five-stage workflow, changing biological data into mathematical comparisons for reliable identification.
Step 1: Enrollment/Capture
This is where the system needs to “meet” you first. Specialized hardware captures your biological signature – fingerprint scanners map your ridge patterns, cameras measure the distances between your facial features. The quality of this first impression matters because garbage in means garbage out forever.
Step 2: Preprocessing
Raw biometric data is like a blurry photo with coffee stains. This step acts like a digital cleanup crew, removing noise and enhancing quality so the system can actually see what it’s working with.
Step 3: Feature Extraction
Here’s where your biology becomes math. The system picks out what makes you uniquely you – those ridge endings on your finger, the exact spacing of your eyes – and converts it all into a compact mathematical recipe that’s uniquely yours.
Step 4: Comparison/Matching
When you come back, the system whips up a fresh mathematical recipe from your new sample and compares it against your stored one. It’s not looking for perfection – it’s calculating how close the match is.
Step 5: Decision
Based on how confident the match is, the system makes the call: you’re in, you’re out, or let’s try that again.
All of this complexity is invisible to users, who experience it as simply “put your finger here” or “look at the camera” – but behind that simplicity is some seriously clever math.
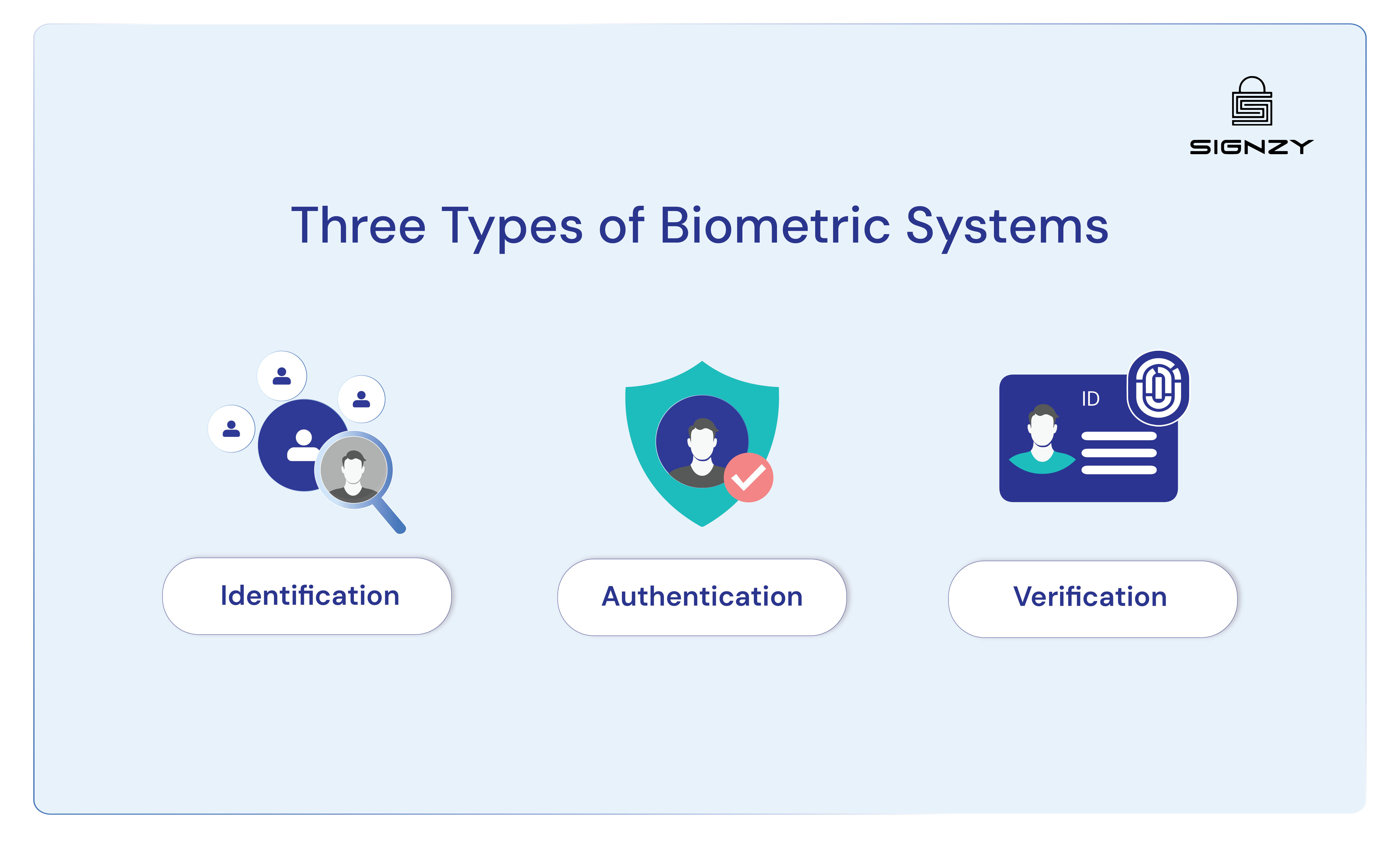
Which Types of Biometric Verification are Most Effective?
The effectiveness of biometric verification depends largely on the specific use case, but the technology generally falls into two main categories:
-
Morphological Biometric Verification
These systems analyze the physical structure and characteristics of your body – the traits you’re born with that remain relatively stable throughout your life. Physical biometrics tend to be highly accurate and difficult to replicate, making them popular for high-security applications.
Here are some examples:
- Fingerprint Recognition – Analyzes ridge patterns and minutiae points on fingertips; widely adopted due to proven accuracy and user familiarity.
- Facial Recognition – Measures geometric relationships between facial features; increasingly popular due to contactless operation and smartphone integration.
- Iris/Retina Scanning – Maps unique patterns in the colored part of the eye or blood vessel patterns in the retina; extremely accurate but requires specialized hardware.
- Hand Geometry – Measures finger length, width, and palm dimensions; less precise but works well in industrial environments.
- Palm Print Recognition – Analyzes palm surface patterns and creases; offers larger surface area than fingerprints for better accuracy.
Physical biometrics offer high accuracy and permanence, but they can be affected by injuries, aging, or environmental conditions that temporarily alter appearance.
-
Behavioral Biometrics Verification
These systems focus on how you naturally perform actions – your unique behavioral patterns that develop over time. Behavioral biometrics can be more dynamic and adaptive, often working continuously in the background without requiring specific user actions.
Here are some examples:
- Voice Recognition – Analyzes vocal patterns, pitch, tone, and speaking rhythm; convenient for phone-based authentication but can be affected by illness or emotion.
- Keystroke Dynamics – Measures typing patterns, speed, and rhythm; useful for continuous authentication during computer use.
- Signature Dynamics – Captures not just signature appearance but pressure, speed, and stroke patterns; familiar to users but can vary with practice.
- Gait Analysis – Studies walking patterns and body movement; promising for surveillance applications but requires sophisticated sensors.
- Mouse Movement Patterns – Tracks how users move and click their mouse; emerging method for continuous web-based authentication.
Behavioral biometrics excel at continuous authentication and are harder to steal since they’re based on learned actions, but they can be less stable than physical traits and may require longer observation periods for accurate identification.
Where are Biometric Systems Being Used Today?
So here’s the thing – if you’ve unlocked your phone with your face today, you’ve already used biometrics. But that’s just scratching the surface of where this stuff has quietly taken over.
- Financial Services – Banks use facial recognition for account access, ATMs with fingerprint authentication, and voice verification for phone banking to reduce fraud while speeding up customer service
- Healthcare – Hospitals implement palm scanning for patient identification, preventing medical errors and ensuring accurate record keeping in critical care situations
- Border Control & Transportation – Airports deploy facial recognition for security screening and expedited boarding, while immigration systems use multiple biometric modalities for visa processing and border crossings
- Workplace Access – Corporate offices use fingerprint or facial recognition for building entry, time tracking, and securing sensitive areas without the hassle of lost keycards
- Mobile & Consumer Devices – Smartphones, laptops, and smart home systems integrate fingerprint, facial, and voice recognition for device unlocking and payment authorization
- Retail & E-commerce – Stores use facial recognition for loss prevention, while online platforms implement voice and behavioral biometrics to prevent account takeovers and fraudulent transactions
- Education – Schools and universities deploy biometric systems for campus access, cafeteria payments, and exam proctoring to ensure student safety and academic integrity
Turns out when something actually works better than the old way of doing things, it spreads pretty fast.
How to Implement Biometrics Identity Verification System?
When it comes to getting biometric verification running in your business, you’ve basically got two options:
- Build the whole thing yourself
- Use ready-made APIs
Most companies automatically think “custom build” because they want control, but that’s usually the harder path.
Building in-house means your team handles everything from hardware selection to algorithm development. You get total control but also months of development time, expensive specialized talent, and all the headaches of maintaining complex infrastructure. Using APIs lets you plug into proven solutions that have already solved the hard problems – you’re up and running in weeks instead of months, with predictable costs and someone else handling the technical complexity.
For most businesses, the API route makes way more sense. At Signzy, we’ve built enterprise-grade biometric verification APIs that you can integrate quickly, letting you focus on your actual business instead of becoming a biometrics expert overnight. If you’d like to know more, book a demo here.
FAQs
How fast do biometric verifications work?
Most biometric authentications complete within 1-3 seconds, including capture, processing, and matching. This speed makes them practical for high-volume applications like airport security or employee access control.
Can biometric data be stolen or hacked?
Systems store mathematical templates, not actual biometric images, making them extremely difficult to reverse-engineer. Even if templates are stolen, they can’t be used to recreate your original fingerprint or face.
What happens if my biometric data changes due to injury?
Most systems can handle minor changes and offer alternative verification methods. Severe injuries may require re-enrollment, but systems typically store multiple samples and can adapt to gradual changes over time.
Are biometric systems expensive to implement?
API-based solutions have made biometric verification affordable for most businesses, with costs often lower than traditional security systems when factoring in reduced password management and fraud prevention.