AML Transaction Monitoring Rules with Examples and Best Practices
July 31, 2025
8 minutes read
- AML transaction monitoring rules set boundaries, spot red flags exceeding limits, route suspicious activity to humans, and generate regulatory reports like SARs.
- Criminals split transactions across wire transfers, ACH, cash deposits, and cards to avoid detection – rules must connect these dots.
- Run new AML transaction monitoring rules against historical data in sandbox environments to prevent false positive floods or missed red flags.
Money laundering is a $2 trillion problem, and your monitoring rules are what stand between criminals and clean money. But here’s the thing – most companies configure these AML transaction monitoring rules wrong. They either catch everything (including legitimate customers) or miss the actual suspicious stuff.
I’ve seen compliance teams spend months tweaking thresholds because someone decided all wire transfers over $10,000 were automatically suspicious.
Spoiler alert: they’re not.
The trick is understanding what suspicion actually looks like for your customers and then building rules that make sense. A construction company moving $50,000 isn’t weird. Is a coffee shop doing the same thing? Maybe worth a look.
After researching this topic and chatting with folks who deal with AML monitoring daily, I’ve got some solid insights to share. Let’s start with nuts and bolts first.
What Are AML Transaction Monitoring Rules?
AML transaction monitoring rules are the automated instructions that tell your system what are the red flag transactions to watch out for. Yeah, that’s a bookish definition; we are going to list what it looks like in practice.
But first, what’s the point of setting up these rules? Actually, there are endless reasons, but for now, these data points should clear things up:
- Criminal networks wash between $800 billion to $2 trillion annually through global financial systems, accounting for 2-5% of worldwide economic activity (United Nations Office on Drugs and Crime)
- Tax evasion schemes cost the government $688 billion in uncollected revenue for 2021, with potential losses reaching $7 trillion over the coming decade. (IRS)
- Cryptocurrency-based criminal activity reached $40.9 billion in 2024 and is projected to hit $51 billion soon. (Chainanalysis, 2024)
So now that we know the problem is serious, it’s now time to see what it looks like in practice:
AML transaction monitoring rules chances of AML fraud by:
- Setting the boundaries (thresholds, behavior patterns, and risk signals).
- Spotting red flags that exceed those limits
- Routing suspicious stuff to humans
- Generating reports for regulatory filings like SARs and STRs.
We are going to discuss these use cases in more detail in the following section. Read on.
Common AML Transaction Monitoring Rule Types with Examples
Every rule has a job. Whether it’s catching risky cash behavior or spotting unusual account patterns, each one plays a role in helping compliance teams focus on what’s actually suspicious.
Let’s walk through the common types of rules and how they work in practice.
Cash Transaction Rules
Structuring is probably the oldest trick in the money laundering playbook. Criminals break large cash amounts into smaller deposits to avoid the $10,000 reporting threshold.
For example, a typical rule here would alert if a customer makes 3+ cash deposits of $9,000-$9,999 within 30 days – because legitimate businesses don’t usually have that exact timing pattern.
Wire Transfer and Cross-Border Rules
International wire transfers are where the real money gets moved, especially when it involves sketchy jurisdictions. Consider this scenario: wire transfers over $50,000 to or from high-risk countries within 24 hours of the initial deposit.
The speed factor matters because launderers often move money fast to create confusion.
Account Activity and Behavioral Rules
When dormant accounts suddenly spring to life, that’s usually worth a look – though it’s not always sinister.
Think about accounts that have been inactive for over 180 days but suddenly receive more than $250,000 in a week. Sure, someone might have sold their house or gotten an inheritance, but you’re also looking at potential money mule operations or compromised accounts.
Third-Party and Relationship-Based Rules
We once had a client plug-in our business verification API to verify onboarded vendors and their payouts. Do you know what they found? Their own branch payroll had onboarded entities with two employees moving over a million dollars a month. No solid documentation, no real office, just money movement and shell paperwork.
That’s exactly what third-party and relationship-based AML rules are meant to catch.
Best Practices for Configuring AML Transaction Monitoring Rules
We already walked you through some rule examples you can pick based on your specific requirements. Now comes the configuration and ongoing maintenance part.
Here are six configuration practices you can follow:
- Establish Complete Customer Identity Verification (KYC) – You can’t monitor what you don’t know. Make sure you’re collecting real customer info upfront – names, addresses, IDs, and business details. If someone’s dodging basic questions or providing sketchy documentation, your rules should flag that immediately.
- Perform Risk-Based Customer Due Diligence (CDD) – Don’t just check the boxes. Understand what your customers actually do, how much money they typically make, and where it comes from. When someone suddenly starts acting completely different from their profile, that’s when your rules need to kick in.
- Configure Customer-Specific Transaction Thresholds – Forget the “$10,000 rule” mentality. A $5,000 transaction might be huge for a small retailer but pocket change for a construction company. Make your thresholds fit the customer instead of a random number.
- Set Velocity and Frequency Limits – Is someone making 47 transactions in one day when they usually do 3 per month? That’s a red flag. Set rules to catch these velocity spikes before they become bigger problems.
- Flag High-Risk Geographic Transactions – Transactions to sanctioned countries are obvious no-gos but also watch for weird geographic patterns. Why is a local pizza shop suddenly sending money to 12 different countries?
- Test Rules in Sandbox Environment Before Deployment – Run your new rules against historical transaction data to see what they would have caught and missed. This prevents going live with rules that either flood you with false positives or miss obvious red flags.
The actual goal isn’t to catch every single suspicious transaction. Just try to catch the ones that matter while keeping legitimate business flowing.
Essential Components of Effective Transaction Monitoring Systems
Let’s start with the basics, aka the rules engine.
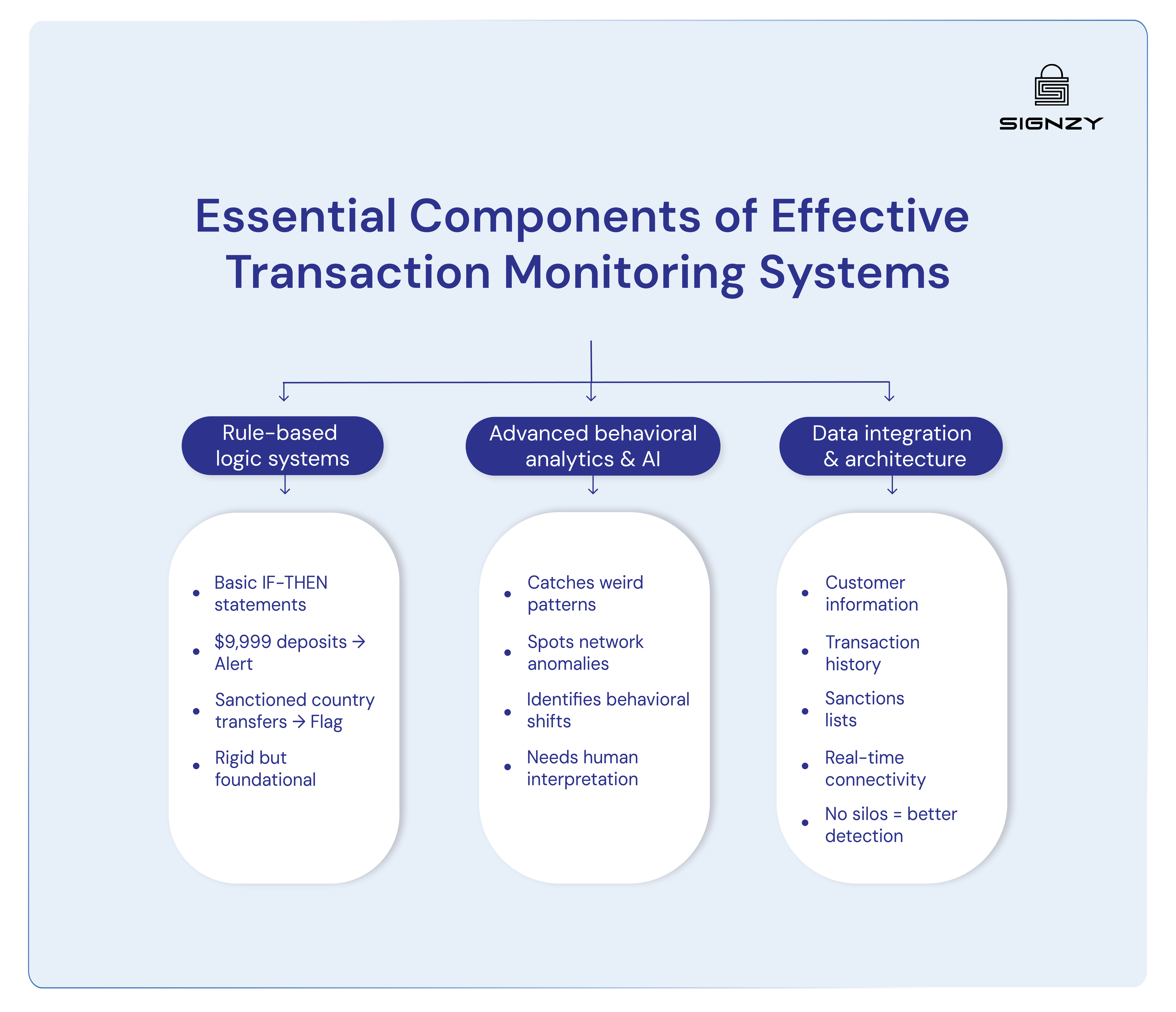
1. Rule-Based Logic Systems
These are your basic IF-THIS-THEN-THAT statements to handle the bread-and-butter suspicious activity that criminals still try to pull. Someone deposits $9,999 five times in a week? Rule fires. Wire transfer to a sanctioned country? Alert goes off.
Of course, they’re a bit rigid but still solid as a foundation. Especially when paired with more advanced layers, such as ML and behavioral analytics.
2. Advanced Behavioral Analytics and AI Integration
Machine learning catches the weird stuff that doesn’t fit neat rules. Like when transaction patterns look normal individually but create suspicious networks when you zoom out.
The AI spots behavioral changes that take humans forever to notice, though you still need people to figure out what it all means.
3. Data Integration and Architecture
Your monitoring is only as good as the data you can actually see. Customer info, transaction history, sanctions lists, risk scores – if they’re sitting in separate systems that don’t talk to each other, you’re basically guessing. Good architecture means everything connects and updates in real-time.
Verifying Customer Information Upfront for Effective Transaction Monitoring
Transaction monitoring rules can be incredibly smart, but they’re only as good as the data they’re working with.
When customers go through basic onboarding processes without thorough verification or when business activities aren’t properly confirmed upfront, even the best monitoring systems struggle to work effectively. For example:
- Individual Customer Issues: People slip through KYC with fake documents or stolen identities. Your monitoring rules think they’re watching legitimate customers when they’re actually tracking fraudsters who shouldn’t have accounts in the first place.
- Business Customer Problems: Companies lie about their industry or business model during onboarding. A crypto exchange calls itself a “consulting firm” and your rules completely miss suspicious patterns because they’re monitoring for the wrong type of business activity.
The fix isn’t smarter monitoring rules – it’s cleaner data going into those rules. When KYC and KYB verification happens properly upfront through automated APIs, your transaction monitoring actually knows who it’s watching.
If you are looking to automate any of these aspects, Signzy’s verification APIs can help you catch these issues during onboarding automatically, so your alerts mean something instead of chasing phantom problems. Book a demo here to know more.
FAQs
What's the difference between rule-based and AI-based monitoring?
Rule-based systems catch known patterns using if-then logic, while AI detects subtle anomalies and behavioral changes that traditional rules miss.
What triggers the most false positives in AML monitoring?
Static dollar thresholds that don’t account for customer risk profiles, causing legitimate high-value customers to generate constant alerts.
Do small financial institutions need transaction monitoring?
Yes, all institutions handling customer funds need AML monitoring. Smaller institutions often use shared systems or cloud-based solutions to reduce costs.
What's the biggest mistake in configuring monitoring rules?
Setting thresholds too low without considering customer profiles, which floods investigators with meaningless alerts while missing actual suspicious activity.