-
- Social Security numbers are nine-digit identifiers that serve as primary keys for tax reporting, employment verification, and background checks.
- Businesses collect SSNs for mandatory payroll processing, tax compliance, background screening, and customer identity verification requirements.
- SSA’s official verification portal at ssa.gov/employer/ssnv.htm provides free government database access for legitimate number checking. However, it may not be scalable.
I was digging through FTC identity theft numbers from the last five years and found something interesting. First, see the data here:
So basically, government document fraud exploded in 2021 (pandemic benefits), credit card fraud stays steady, and employment fraud bounces around.
So what caught my eye?
Social Security Numbers.
Well, you won’t see SSNs mentioned anywhere in the chart, but if you reverse engineer things a bit, many of these most-reported frauds can start with just a leaked Social Security Number.
- Need to file a fake unemployment claim? Gotta have the SSN.
- Want to open credit cards in someone else’s name? SSN makes it way easier.
- Applying for jobs with a stolen identity? You’re going to need that nine-digit number.
This creates a weird situation.
You collect Social Security numbers because you have to – payroll, background checks, tax forms. But every SSN in your files is basically a skeleton key for identity thieves.
So what can you actually do about it? After digging into this, I found five practical methods that work. Won’t stop everything, but they’ll shut down most SSN thieves before they get started.
5 Methods to Protect Your Business From Social Security Identity Theft
The first four methods help you catch fraudulent Social Security numbers before they enter your business systems. The fifth method acts as your ongoing filter to catch problems that might have evolved or slipped through your initial checks.
-
Verify SSN Before Processing Using the Official Government Portal
Check with the source before you process anything – the SSA’s verification system catches fake numbers before they create problems in your business.
- Go to https://www.ssa.gov/employer/ssnv.htm
- Register for the Social Security Number Verification Service (SSNVS) using your business EIN.
- Input the name and SSN combination you want to verify through the secure portal.
- Check if the name matches SSA records or if there are discrepancies that need investigation.
- Don’t proceed with onboarding when names don’t match SSN records in the system.
- Keep records of verification requests and results for compliance audits and fraud pattern tracking.
This stops most basic identity theft attempts right at the front door. Legitimate applicants won’t have problems with government verification, but criminals using stolen SSNs get caught immediately.
-
Establish Comprehensive Employee Training Protocols
Your team needs to know what Social Security fraud actually looks like when it walks through your door. Most identity theft succeeds because employees don’t recognize the warning signs or don’t know how to respond when something seems off.
Training should cover spotting tampered Social Security cards, recognizing documentation that doesn’t match, and understanding when to escalate suspicious situations. Create clear procedures so employees know exactly who to contact and what steps to take when red flags appear.
-
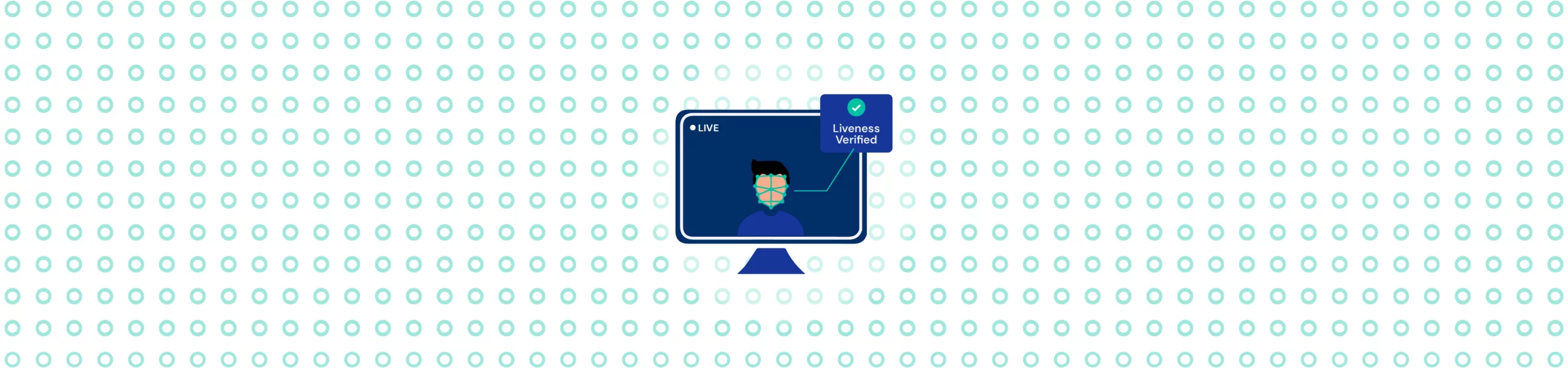
Use Face Match and Liveness Detection
Biometric verification makes it nearly impossible for criminals to use stolen documents with someone else’s photo or information.
| Technology Component | How It Works | Fraud Prevention |
| Facial Recognition | Compares live photo with government ID photo | Prevents the use of stolen documents with a different person’s photo |
| Liveness Detection | Confirms the person is physically present during verification | Stops criminals from using photos or videos of a legitimate person |
| Document Authentication | Scans ID for security features and tampering | Catches fake or altered government documents |
| Biometric Binding | Links facial features to SSN and employment records | Creates a unique identity profile that’s difficult to replicate |
This technology catches sophisticated fraud attempts that might fool human reviewers. Even if criminals have high-quality fake documents, they can’t fake being the actual person whose identity they’re trying to steal.
-
E-Verify Employment Authorization
E-Verify connects directly to government databases and catches SSN misuse in real-time. The system flags when Social Security numbers are being used by multiple people or don’t match government employment records.
While not mandatory for all businesses, E-Verify provides verification that catches identity theft attempts that pass other checks. It also protects your business from unknowingly hiring unauthorized workers using stolen SSNs, which can result in penalties and legal problems.
-
Conduct Reverification Routinely
Regular reverification catches problems that develop after someone’s already in your system. By then, identity thieves may have already caused damage, so routine checking helps you spot issues before they become major problems.
Some of the best practices you can follow are:
- Run annual SSN verification checks – Use the same SSA portal to reverify that existing employee SSNs haven’t been flagged
- Monitor payroll for duplicate SSNs – Check if the same Social Security number appears on multiple employee records
- Flag sudden banking changes – Review when employees change direct deposit accounts, especially multiple times
- Watch for address pattern changes – Notice when employees frequently update their home addresses without logical reasons
- Cross-check tax withholding modifications – Investigate when employees make unusual changes to their W-4 information
- Review high-access employees quarterly – Verify identity more frequently for staff with financial or data system access
- Check during performance reviews – Include identity verification as part of annual employee evaluation processes
That covers the main protection methods. But honestly, even with good systems in place, life happens. You might accidentally accept a stolen SSN, or an employee or customer becomes an identity theft victim after they’re already working for you.
The next section will answer what to do when your prevention methods weren’t enough.
Immediate Steps When SSN Theft Occurs
First thing to understand – this isn’t just about the person whose SSN got stolen. Your business faces potential liability, compliance issues, and reputation damage.
Plus, criminals often don’t stop at one stolen identity, so you’re likely dealing with a bigger problem than what you initially discovered.
Here’s an eight-step process you can follow.
- Secure the compromised data immediately: Lock down access to the affected employee records and any systems containing the stolen SSN information.
- Document everything you find: Create a detailed record of when you discovered the theft, what information was compromised, and who had access to it.
- Contact the affected individual: Inform the person whose SSN was stolen and provide them with identity theft resources and next steps.
- Freeze the employee’s accounts: Suspend payroll, benefits, and system access for the compromised identity until you can verify legitimate ownership.
- Report to law enforcement: File a report with local police and contact the FBI’s Internet Crime Complaint Center for a federal investigation
- Notify your insurance carrier: Contact your cyber liability or business insurance provider to report the incident and understand coverage options.
- Preserve evidence: Don’t delete or modify any records related to the theft, as law enforcement and insurers will need this information.
- Check for additional victims: Review other recent hires or applications for similar patterns that might indicate broader identity theft.
Acting quickly doesn’t just limit damage – it shows employees, customers, and regulators that you take identity protection seriously.
The longer you wait, the more complicated and expensive the cleanup becomes.
Use Technology to Prevent SSN Theft
Checking SSNs one by one through government portals works fine until you’re dealing with hundreds of customers and employees. Then it becomes a nightmare of spreadsheets and manual work that slows everything down.
The solution is automated SSN verification through APIs that connect directly to government databases. Instead of manually entering each Social Security number and waiting for results, these systems verify SSNs in real-time during your application process.
We, at Signzy, have actually built one that plugs directly into your existing infrastructure without requiring any custom development. If you want to see how it works in practice, book a demo here.
FAQs
How often should I verify Social Security numbers in my business?
Verify SSNs immediately during onboarding and conduct routine reverification quarterly for employees, annually for customers. High-risk positions or suspicious activity may require more frequent checking.
What happens if I accidentally hire someone using a stolen Social Security number?
You’re required to terminate employment immediately, report the incident to authorities, and may face penalties. Document everything and contact law enforcement and your insurance carrier promptly.
Do I need to verify Social Security numbers for independent contractors?
Yes, you need valid SSNs for 1099 reporting and tax compliance. Verify contractor SSNs the same way you would employees to prevent tax filing issues and fraud.
What should I do if an employee reports their SSN was stolen?
Freeze their payroll accounts, help them contact credit bureaus and the SSA, document the incident, and reverify their identity using alternative methods before restoring access.